Originally posted by Christina Bonnington and Spencer Ackerman on Wired.com, August 30, 2012
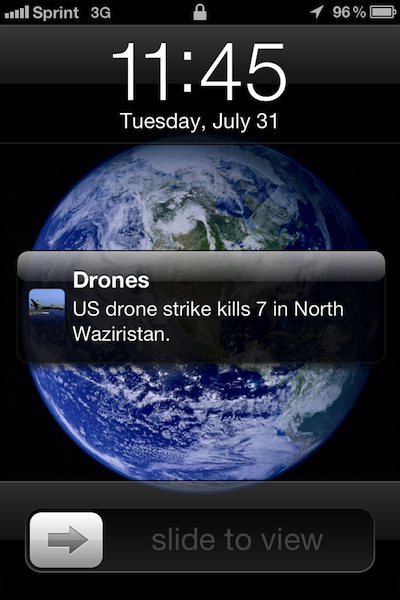
It seemed like a simple enough idea for an iPhone app: Send users a pop-up notice whenever a flying robots kills someone in one of America’s many undeclared wars. But Apple keeps blocking the Drones+ program from its App Store — and therefore, from iPhones everywhere. The Cupertino company says the content is “objectionable and crude,” according to Apple’s latest rejection letter.
It’s the third time in a month that Apple has turned Drones+ away, says Josh Begley, the program’s New York-based developer. The company’s reasons for keeping the program out of the App Store keep shifting. First, Apple called the bare-bones application that aggregates news of U.S. drone strikes in Pakistan, Yemen and Somalia “not useful.” Then there was an issue with hiding a corporate logo. And now, there’s this crude content problem.
Begley is confused. Drones+ doesn’t present grisly images of corpses left in the aftermath of the strikes. It just tells users when a strike has occurred, going off a publicly available database of strikes compiled by the U.K.’s Bureau of Investigative Journalism, which compiles media accounts of the strikes.
iOS developers have a strict set of guidelines that must be adhered to in order to gain acceptance into the App Store. Apps are judged on technical, content and design criteria. As Apple does not comment on the app reviews process, it can be difficult to ascertain exactly why an app got rejected. But Apple’s team of reviewers is small, sifts through up to 10,000 apps a week, and necessarily errs on the side of caution when it comes to potentially questionable apps.
Apple’s original objections to Drones+ regarded the functionality in Begley’s app, not its content. Now he’s wondering if it’s worth redesigning and submitting it a fourth time.
“If the content is found to be objectionable, and it’s literally just an aggregation of news, I don’t know how to change that,” Begley says.
Begley’s app is unlikely to be the next Angry Birds or Draw Something. It’s deliberately threadbare. When a drone strike occurs, Drones+ catalogs it, and presents a map of the area where the strike took place, marked by a pushpin. You can click through to media reports of a given strike that the Bureau of Investigative Reporting compiles, as well as some basic facts about whom the media thinks the strike targeted. As the demo video above shows, that’s about it.
It works best, Begley thinks, when users enable push notifications for Drones+. “I wanted to play with this idea of push notifications and push button technology — essentially asking a question about what we choose to get notified about in real time,” he says. “I thought reaching into the pockets of U.S. smartphone users and annoying them into drone-consciousness could be an interesting way to surface the conversation a bit more.”
But that conversation may not end up occurring. Begley, a student at Clay Shirky’s lab at NYU’s Interactive Telecommunications Program, submitted a threadbare version of Drones+ to Apple in July. About two weeks later, on July 23, Apple told him was just too blah. “The features and/or content of your app were not useful or entertaining enough,” read an e-mail from Apple Begley shared with Wired, “or your app did not appeal to a broad enough audience.”
Finally, on Aug. 27, Apple gave him yet another thumbs down. But this time the company’s reasons were different from the fairly clear-cut functionality concerns it previously cited. “We found that your app contains content that many audiences would find objectionable, which is not in compliance with the App Store Review Guidelines,” the company e-mailed him.
It was the first time the App Store told him that his content was the real problem, even though the content hadn’t changed much from Begley’s initial July submission. It’s a curious choice: The App Store carries remote-control apps for a drone quadricopter, although not one actually being used in a war zone. And of course, the App Store houses innumerable applications for news publications and aggregators that deliver much of the same content provided by Begley’s app.
Wired reached out to Apple on the perplexing rejection of the app, but Apple was unable to comment.
Begley is about at his wits end over the iOS version of Drones+. “I’m kind of back at the drawing board about what exactly I’m supposed to do,” Begley said. The basic idea was to see if he could get App Store denizens a bit more interested in the U.S.’ secretive, robotic wars, with information on those wars popping up on their phones the same way an Instagram comment or retweet might. Instead, Begley’s thinking about whether he’d have a better shot making the same point in the Android Market.
Drones+ iPhone App from Josh Begley on Vimeo.








 sending...
sending...
